This guide offers an overview of SSL certificate installation on the Apache web server, which is among the most widely used web servers. Given that there are two versions of the Apache web server (“httpd” for RHEL-based Linux distributions and “apache2” for Debian-based Linux distros), we provide instructions for SSL certificate installation for both versions.
For SSL installation on both, the following files are needed:
- SSL certificate – a PEM-formatted file (the usual extensions are .pem, .crt, .txt) which can be downloaded from your 1Byte account or from the email you received from Sectigo CA.
- Private key – a code (or file with the code, the usual extensions are .key, .pem, .txt) which is generated along with the CSR code used for SSL activation. If it was generated on the server, it will be located in the same folder that the generation command was run in, unless a different location was specified manually.
- CA Bundle – a file with several other certificate codes (intermediate and root certificates of the SSL chain of trust) provided along with the SSL certificate file in your email from Sectigo and in your 1Byte account.
Checking Linux distribution type
If you have an RHEL-based Linux distro (CentOS, RedHat, etc.), go here: SSL Certificate installation on httpd.
If you are not sure which Linux distro you have or which version of Apache is being used, run one of the following commands:
httpd -S or apachectl -S
(httpd is an Apache package for RHEL-based Linux Distros, whereas apachectl is for Debian-based systems).
If the “Command not found” message is shown, try another option. The command that gives you an output with the server setup details will determine your distro and Apache type. Once you figure out which type you have, head to the corresponding installation guide.
Uploading SSL files to the server
Before starting the installation, the certificate files should be uploaded to the server. There are a number of ways to upload SSL files to the server. In this guide, we will mention the two most popular methods: FTP and manual upload via SSH.
FTP
FTP protocol can be used to transfer files to the server. It’s recommended that you place the certificate files in the same directory so that you will not lose them. For example, you can place them in the following location: /etc/ssl
Manual upload via SSH
You can manually create a file on your server and paste the necessary SSL contents over SSH.
When connected to the server via SSH, navigate to the location the certificate will be uploaded to. We recommend gathering all of the files in one directory, so that you will not lose them. For example, you can place them in the following location: /etc/ssl
After that, you need to create an empty file. Usually, the commands cat yourfilename, touch yourfilename, nano yourfilename or vim yourfilename can be used for this purpose.
Once the empty file is created and opened for editing, please copy the SSL file contents from your local machine and paste them to the opened file. Make sure to save the file when you’re done.
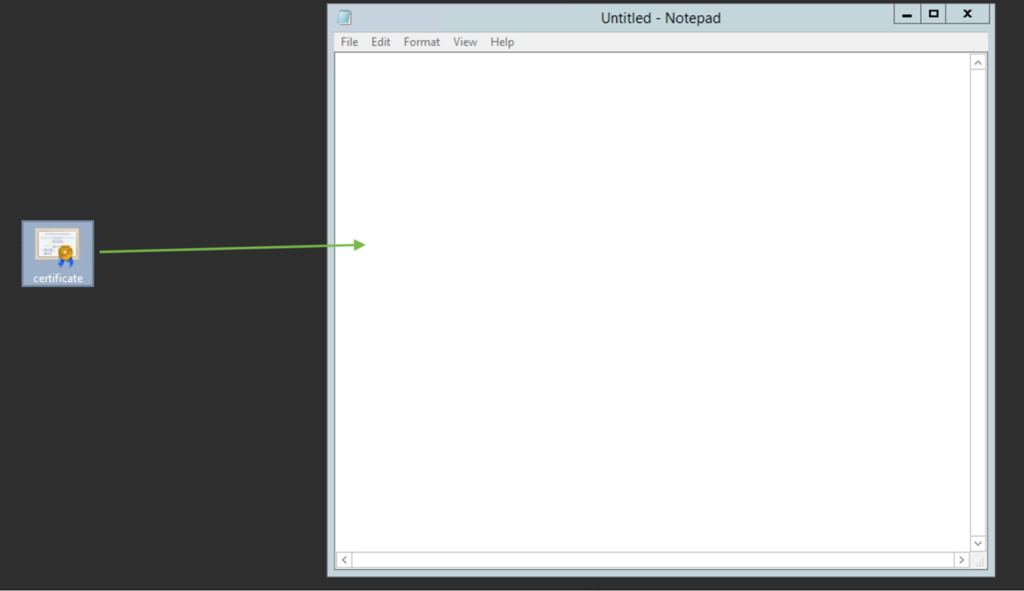
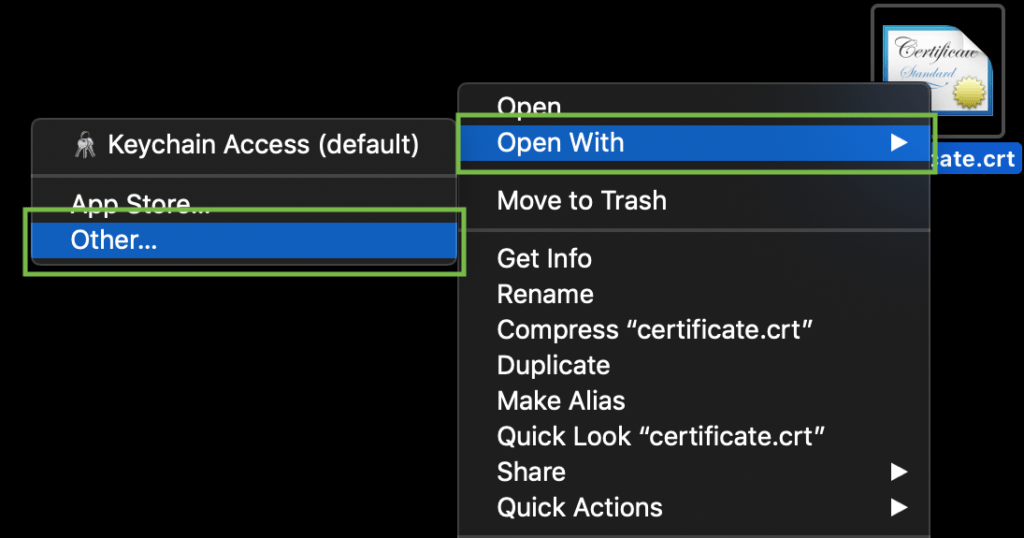
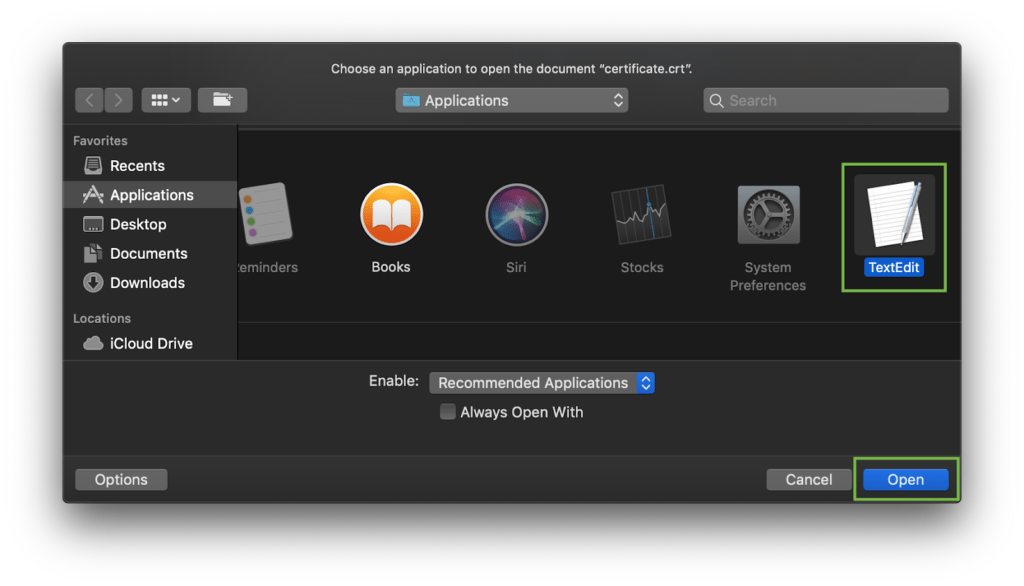
To check the contents of the SSL files on your PC or Mac, you can drag and drop them to Notepad (if on Windows) or open them using TextEdit (if on macOS).
Windows:
bytemacOS:
Press “Control” key click on the file:
As an example, let’s take a look at creating a file via command cat. You can create files on the server and paste in contents by entering the following command:
cat >> filename
For example, let’s create our certificate file on the server:
When the command is entered, paste the certificate code into the terminal/SSH client.
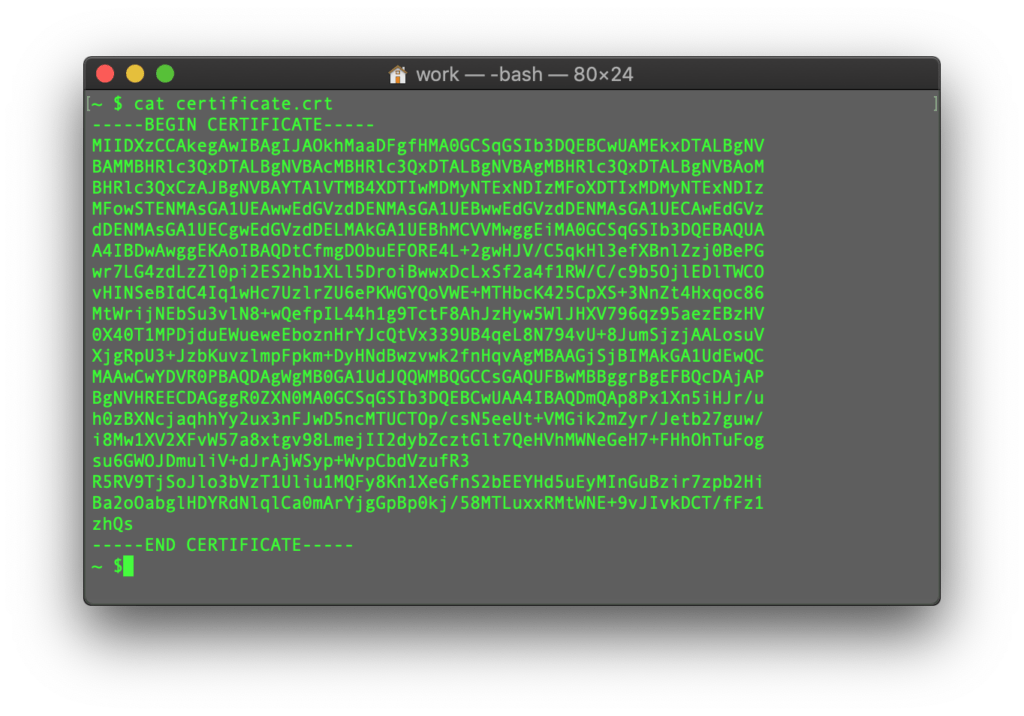
Ensure there’s no empty line at the end and press CTRL+D to save the file.
You can check the contents of the newly created command by typing the next command:
cat filename
You may repeat the process with the CA Bundle file and the Private key file (if the CSR code and Private key were generated in another place, not on this server, and you need to move the Private key to the server manually).
Select the guidelines on your further SSL installation steps depending on exact server type: