Web-based aaPanel Management’s “Security ” sidebar menu will be the topic of this post. Before getting started, read this article about Uploading your Website with aaPanel.
5 Steps to Safety Management In aaPanel
FURTHER READING: |
| 1. aaPanel Mail Server Setup with RoundCube Webmail |
| 2. How To Install WordPress and Create Website in aaPanel? |
| 3. 9 Common Settings of aaPanel |
1. SSH Settings
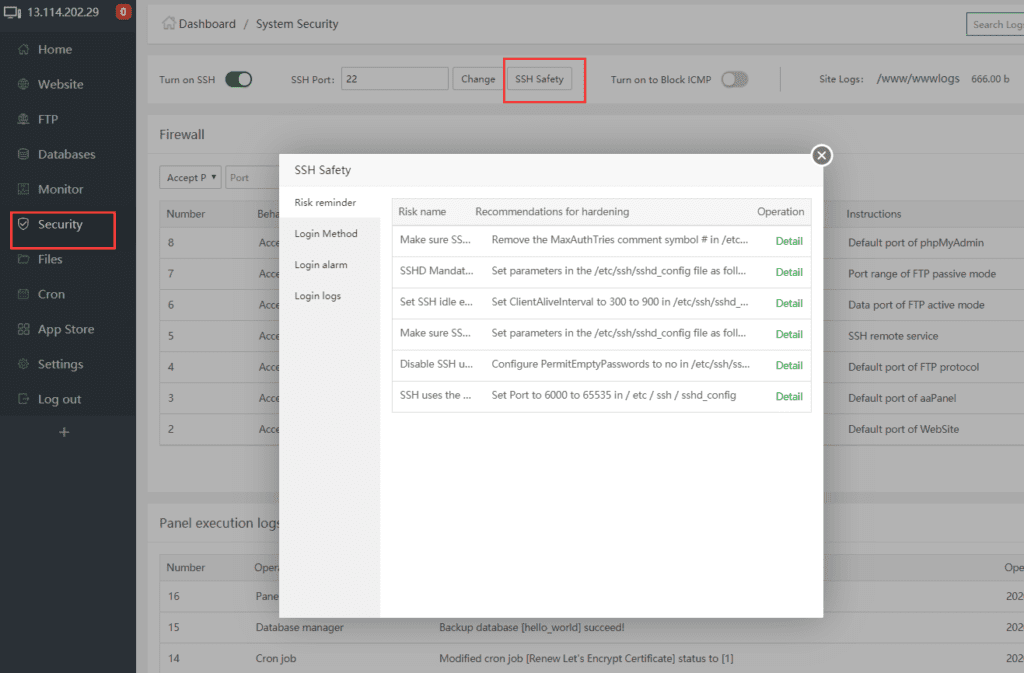
Features:
- Allow/block your ssh port connection
- Change your ssh port
- Check your ssh service risk
- Set up a certificate to connect to ssh
- Monitor ROOT login and send a login reminder
2. Prevent using ping to Server
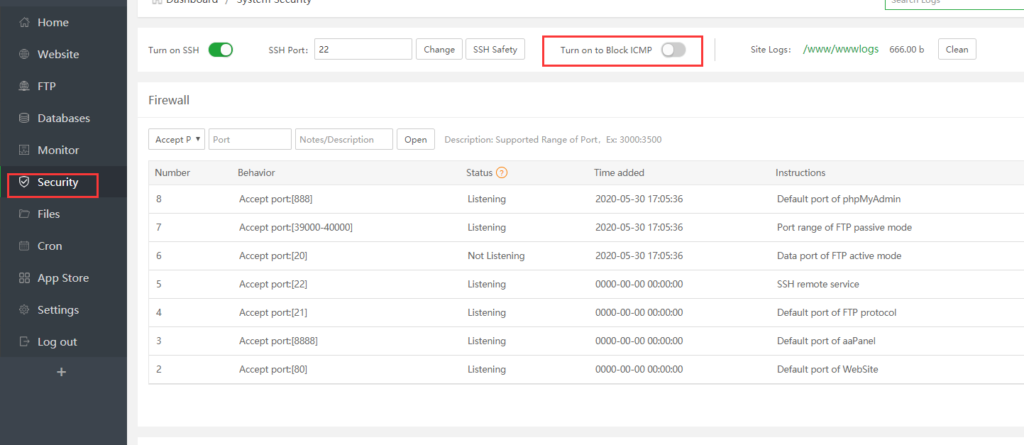
Forbid public IP to ping our server IP
3. Release Ports
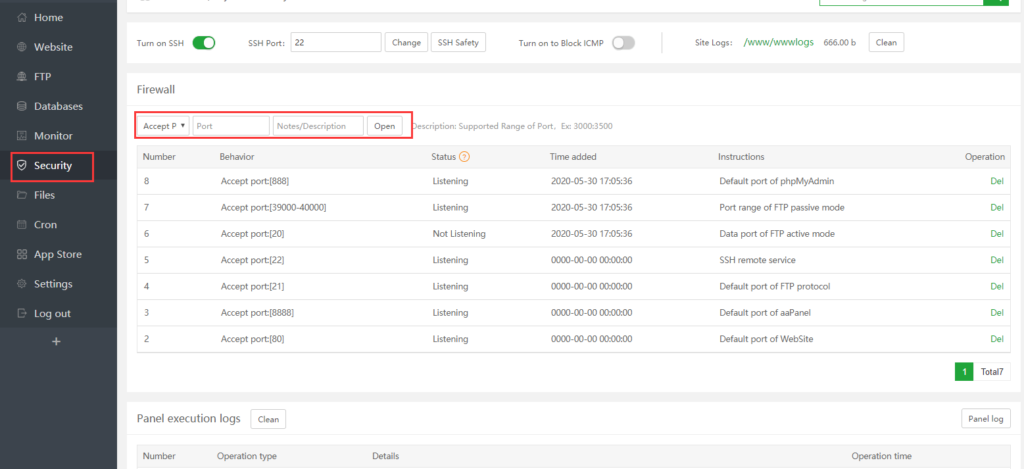
You need to put in the port that needs to be released, as well as its name, to get the port out of your computer.
After the port has been released, you can look at the firewall list to see how the port is working, and the port status.
- Centos6 uses iptables.
- Centos7 uses a firewall.
- Debian / ubuntu uses ufw.
State Description: Not Listening
- There is currently no service program listening on this port!
- The service program using this port is not started!
- This port is obsolete. If it is determined that the port is obsolete, you can delete it directly!
Listening
- The service is listening normally
More functions can be implemented in the system firewall plug-in
4. Block IP
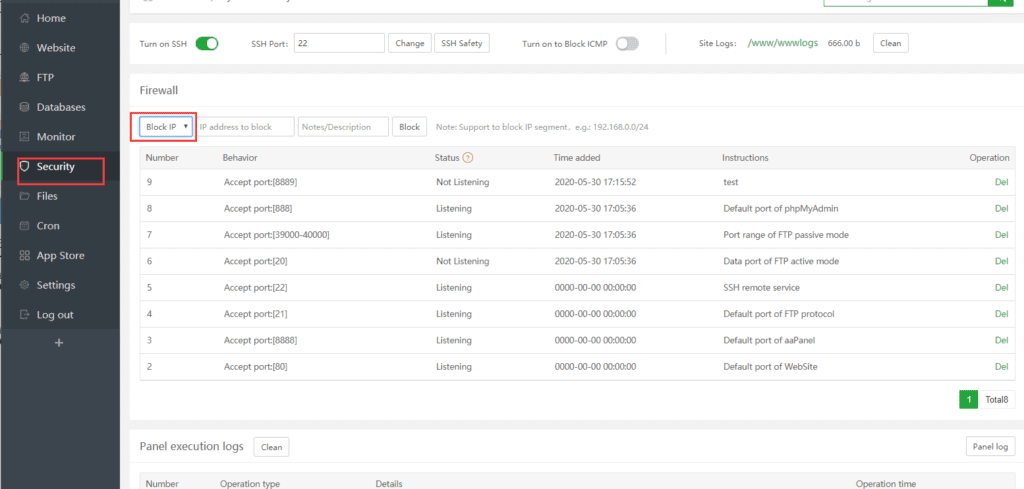
Block IP addresses to prevent malicious attacks or unauthorized access to a given IP address. After successfully blocking an IP address, you may check the firewall list to determine the current state of IP blocking.
Block IP segment rules:
- IP segment: 10.0.0.1-10.0.0.255 Representation: 10.0.0.0/24
- IP segment: 10.0.0.1-10.0.255.255 representation method: 10.0.0.0/16
- IP segment: 10.0.0.1-10.255.255.255 Representation: 10.0.0.0/8
More functions can be implemented in the system firewall plug-in
5. Panel operation log
Specifically, log the current panel action, such as adding a site to the panel, adding a database, and the panel login record, etc., which may be used to determine whether someone signed in and operated maliciously. By clicking the Panel log button, you may view the panel’s error log.

